James the Clark was a machinist by profession, but he had a murky history. According to the Associated Press, in 1968 he was arrested for attempting to arrange a massive counterfeit money deal with contacts in Europe that would have put $50 million phony bills into circulation.

In the 1980s, police in Ohio as well as the FBI spent years chasing the man with the ponytail. Unlike a lot of criminals, he didn’t brandish a gun, resort to violence, or put innocent people in his crosshairs. What he did instead was become the most prolific safecracker in modern times, able to breach what was once believed to be the impenetrable, unbreakable strongbox housed in the country’s 1.8 million payphones. Using means that baffled even security experts, the “payphone bandit” or “telephone bandit” eluded capture. Quarter by quarter and year after year, he collected an estimated $500,000 to $1 million from these tiny safes.
The question was how anyone was ever going to find him. “Unless somebody gets lucky, he’ll probably never get caught,” Ohio Bell Telephone security official Robert Cooperider told The Los Angeles Times in 1987. “He’s well-organized, he’s smart, and he’s not greedy. He only hits a few widely spaced spots each day. He’s always looking over his shoulder, to see if there is a police car, or a telephone company vehicle.”
Though it’s hard to imagine today, there was once a time when making a telephone call meant going home, asking to use someone’s phone, or plunking a quarter into a freestanding payphone. (Or more than one, depending on where you were calling and for how long.) The first public pay-to-use coin-operated phone debuted in Hartford, Connecticut, in 1889. It relied on the honor system, with users depositing coins owed after their call was done. Over the next century, they appeared everywhere, from convenience stores to diners to bus stations. Some were freestanding; others were located inside of a booth to give callers some privacy.
While the phones varied somewhat in design, virtually all of them took care to make the coinbox virtually impregnable. Bell, then the world’s largest phone carrier, reportedly spent years refining a lock on their box that was thought to be unpickable. If a would-be thief wanted to even have a shot at getting into the box, they’d have to try smashing it open with a sledgehammer or knock it out of the ground with a tractor. Given that the boxes only held about $150 when full, few criminals thought it was worth the effort.
James Clark wasn’t one of those people. The Akron, Ohio, native was a machinist by trade, but he had an unsavory history. According to the Associated Press, in 1968 he was arrested for attempting to arrange a massive counterfeit money deal with contacts in Europe that would have put $50 million phony bills into circulation. He was caught and sentenced to three years in prison.
Roughly a decade later, in the early 1980s, Clark devised a new scheme. According to authorities, Clark obtained locks like the ones found on payphones and created a set of specialized locksmith tools that allowed him to pick the lock. Though different operators had somewhat different lock configurations, Clark zeroed in on specific designs to breach. (His exact toolset and technique has never been publicly disclosed, likely due to security concerns.)
Clark’s strategy was simple. Upon arriving at a payphone, he used a custom tool that he could slip into the margins of the coinbox to gauge how much money was inside and whether it was worth pursuing. If it was full, he’d pick up the receiver and pretend to be deep in a conversation. While hunched over the phone, he’d grab his lockpicking tools—which he concealed with an untucked shirttail—and get to work on the lock. Picking one took about 15 minutes. When he got it, the faceplate in front of the coin receptacle came off. Clark would take the box full of change and then replace the faceplate. This last step was key: The phone would continue to operate without the box, giving no physical or mechanical clue it had been tampered with. No one would realize the box was missing until a phone company employee came to retrieve the money—in some cases a week or so later.
The above is the detailed content of The Man Who Robbed 1.8 Million Payphones, Quarter by Quarter. For more information, please follow other related articles on the PHP Chinese website!
 Tokenized Treasuries Near $6B Milestone, Led by BlackRockApr 19, 2025 am 11:44 AM
Tokenized Treasuries Near $6B Milestone, Led by BlackRockApr 19, 2025 am 11:44 AMThe value of blockchain-based U.S. Treasuries is closing in on a new milestone, with total holdings approaching $6 billion.
 title: Canary Capital Is Launching a TRX-Tracking ETFApr 19, 2025 am 11:42 AM
title: Canary Capital Is Launching a TRX-Tracking ETFApr 19, 2025 am 11:42 AMCanary Capital is looking to launch an exchange-traded fund (ETF) tracking the price of Tron's native token, TRX, according to a filing.
 Solana Stablecoin Market Cap Hits Record $12.73 Billion as Sui Supply Reaches $800M with $60M InflowsApr 19, 2025 am 11:40 AM
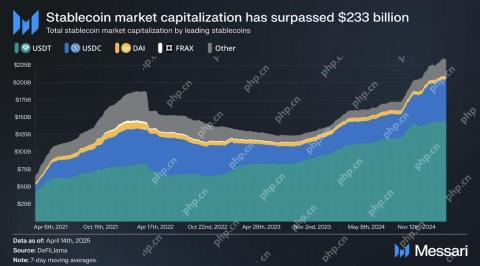
Solana Stablecoin Market Cap Hits Record $12.73 Billion as Sui Supply Reaches $800M with $60M InflowsApr 19, 2025 am 11:40 AMThe stablecoin market has surpassed a total capitalization of $233 billion. Within this sector, Solana's stablecoins have reached a new all-time high market capitalization of $12.73 billion
 Canary Capital Files for Staking TRX ETF, Targeting Launch Before Spot Bitcoin ETFsApr 19, 2025 am 11:38 AM
Canary Capital Files for Staking TRX ETF, Targeting Launch Before Spot Bitcoin ETFsApr 19, 2025 am 11:38 AMCanary Capital is looking to get the U.S. Securities and Exchange Commission's sign-off for an exchange-traded fund that would track the Tron token TRX and has a staking component.
 MoonPay CEO Ivan Soto-Wright calls on US lawmakers to leave a path open to state-level regulators when passing legislation on stablecoinsApr 19, 2025 am 11:36 AM
MoonPay CEO Ivan Soto-Wright calls on US lawmakers to leave a path open to state-level regulators when passing legislation on stablecoinsApr 19, 2025 am 11:36 AMIn an April 18 X post, Soto-Wright said he wanted Congress to “keep state-regulated issuers in the game” when it comes to stablecoin regulation, referencing efforts in the House of Representatives and Senate to create a federal regulatory framework.
 Michael Saylor Dissects the Philosophy and Technological Potential of Bitcoin in '21 Truths of Bitcoin'Apr 19, 2025 am 11:34 AM
Michael Saylor Dissects the Philosophy and Technological Potential of Bitcoin in '21 Truths of Bitcoin'Apr 19, 2025 am 11:34 AMSaylor's ideas centre on the fixed 21 million coin supply of Bitcoin. He presents this shortage as a revolutionary economic idea rather than only a technical one.
 Official Trump (TRUMP) memecoin unlocked 40 million tokens, worth around $300 millionApr 19, 2025 am 11:32 AM
Official Trump (TRUMP) memecoin unlocked 40 million tokens, worth around $300 millionApr 19, 2025 am 11:32 AMThe TRUMP memecoin has gained significant popularity on the Solana network primarily due to its direct affiliation with the U.S. President Donald Trump.
 TRUMP (TRUMP) memecoin unlocks 40 million tokens, worth around $300 millionApr 19, 2025 am 11:30 AM
TRUMP (TRUMP) memecoin unlocks 40 million tokens, worth around $300 millionApr 19, 2025 am 11:30 AMThe TRUMP memecoin has gained significant popularity on the Solana network primarily due to its direct affiliation with the U.S. President Donald Trump.

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

WebStorm Mac version
Useful JavaScript development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.





