Your work IT colleagues probably seem a bit grumpy sometimes, and there's a reason: They're always busy working behind the scenes to keep you secure from hackers and other digital threats. You can make them less grumpy (and improve your own online security outside the office too) by following these tips.
Don't Open Links in Emails That Lead to a Login Screen
It's pretty common to receive an email with a link or a button that leads to a login screen, but you shouldn't use them. It's all too easy for a scammer to create their own fake login screen, email you a convincing looking email with a link, and then steal your password using it.
Instead, if you click on a link that lands you at a login page, close the browser tab or window, open a fresh one, and type in the address for the website yourself (or, if you're using an app, re-open it). Once you've logged in to the right website, you can check your notifications from your account there.
Use Strong Passwords and Two-Factor Authentication (And Don't Share Them!)
 Google
Google You should always use a unique password for every website, service, or app you use, and make sure they are strong.
If you re-use passwords for different services and one of them is breached, the hackers will try the password they stole on other sites to see if you reused it (this is called "credential stuffing"). If you give your logins to a friend (even for your Netflix account), it's out of your control, and they might accidentally disclose it to someone else, leading to additional accounts being compromised in a chain of attacks.
Of course, you can't be expected to remember all of these different passwords, so you should use a password manager to keep track of them. You should also enable two-factor authentication wherever possible, so that even if your password is leaked, attackers still won't be able to access your accounts.
Don't Ignore Windows Security Prompts (UAC)
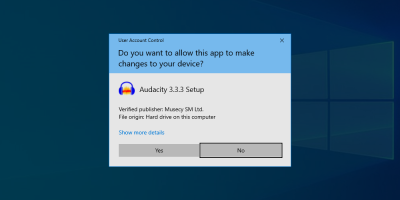
Every Windows user has seen these annoying security prompts from User Account Control (UAC). Whenever a change needs to be made to the system, one of these alerts will pop up and ask an Administrator to approve the action. While they're annoying, you shouldn't ignore them, and carefully read the information they display before dismissing them or allowing the change.
This is because viruses and malware will usually need some kind of Administrator access to burrow deep into your system. These prompts are designed to stop them from doing this. Make sure you check that the application requesting access is from a verified publisher, and from a source you trust. Importantly, make sure you understand why the prompt has been triggered: if a UAC security prompt pops up from an unknown program or when you haven't taken any action, you should decline it and check your system for viruses.
Keep Your Work and Private Life Separate
You don't want your employer to know all the details about your personal life, and your employer doesn't want you to be accidentally leaking company information through your social media profiles. Keep your work and private lives separate by using different email accounts and profiles for each. This helps prevent information from leaking, for example, by making it more difficult for you to accidentally put your dating schedule in the work calendar, or email a sensitive financial report to your yoga class.
The most effective way to do this is to create separate user accounts on your computer. You can also use Firefox Containers or Safari Profiles, or isolate different activities by using a different browser for each.
Set a Passcode On All Of Your Devices
Your phone, tablet, and laptop all contain sensitive information, and they provide access to your bank accounts, credit cards, and other financial tools. If one of them is lost or stolen, whoever gets hold of it can do a lot of damage in a short amount of time.
That's why it's important to set a secure passcode for all of your devices, so that if it leaves your control, it can't be used by anyone else. You can set a passcode on your iPhone or iPad, or your Windows or Android devices.
If your device is stolen, you should remotely wipe it if it is supported on your iOS or Android device.
If Someone Asks For Something Out Of The Usual, Check In With Them
Impersonation scams—where a scammer impersonates your friend, family member, or colleague to get you to send them money or information—are becoming increasingly common. Scammers can even use AI tools to impersonate voices, so if someone texts, emails, or even calls you with an unusual request for money or information (which could be used for later scams), find another way to contact that person to confirm that it's actually them asking.
The best way to do this is to contact them via another communication method. If you receive a suspicious email from a known address, give that person a call directly to confirm that they've asked. If you receive an odd phone call claiming to be from someone you know, hang up and drop them a WhatsApp to check if they made the call before calling them back.
Don't Download Strange Software or Attachments, and never Run Macros
Viruses masquerading as legitimate downloads are everywhere on the Internet, just waiting for someone to click on them. Avoid unknown sources of apps and stick to Apple, Android, and Windows App stores whenever you can.
If you receive an email with a strange or unexpected attachment, don't open it, and confirm that the sender is trusted and intentionally sent the attachment. And, under no circumstances should you run macros from a Microsoft Office document emailed to you: They're almost never something people use outside of work, and if you're at work, your IT department should manage which macros are trusted.
Use Antivirus and Stay Up-To-Date

Installing a good antivirus package is a proactive measure that you can take to help prevent malware from getting onto your devices. Windows Defender is a good, free, default option that ships with Windows 10 and 11. Commercial antivirus suites offer additional functionality like VPNs for extra protection.
Learn How to use Windows and Your Other Software And Devices
Your life will be easier if you know how to use your phone, tablet, and laptop properly. It might take a bit of a time investment, but it'll pay off: you'll be able to do things faster, make less mistakes, and you'll know when something isn't working properly. When you can tell that something isn't quite working as it should, you can investigate by running a virus scan, or seek expert help to resolve the problem.
If there's something tech related you aren't sure about, you can search our thousands of articles and find the answer from one of our experts. You can also subscribe to our newsletter to stay up to date with all the latest gadgets, apps, and feature updates.
Don't Panic!

If something isn't working as expected on your device, stay calm. Don't start mashing buttons or swiping all over the place, as you'll only lose track of where you are or make things worse. By randomly tapping on alerts and notifications in frustration, you could grant a virus access to something accidentally (for example, by allowing one of the UAC prompts discussed above).
If you're really having trouble, contact your IT department (or your nephew, or your tech-obsessed friend), and have them help walk you through fixing the problem. If you need to attempt a fix yourself, our tips on cybersecurity, and computer security best practices are a great place to start.
The above is the detailed content of 10 Security Tips Your IT Department Wishes You\'d Follow. For more information, please follow other related articles on the PHP Chinese website!
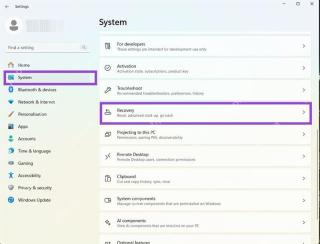 How to Rollback Windows 11 UpdateMay 12, 2025 pm 08:01 PM
How to Rollback Windows 11 UpdateMay 12, 2025 pm 08:01 PMIs Windows 11 update causing system problems? Don’t panic! This article provides three methods of rollback updates to help you restore system stability. Method 1: Rollback updates through Windows settings This method is suitable for users whose update time is less than 10 days. Step 1: Click the "Start" menu to enter "Settings". You can also press the Windows key I on the keyboard. Step 2: In Settings, select System, and then click Recover. Step 3: Under Recovery Options, find "Previous Windows Versions". If the Back button is clickable, the system can be rolled back to the previous version. Step 4: The system will ask you why the rollback is
 13 Windows Keyboard Shortcuts I Couldn't Live WithoutMay 12, 2025 am 03:02 AM
13 Windows Keyboard Shortcuts I Couldn't Live WithoutMay 12, 2025 am 03:02 AMMastering Windows keyboard shortcuts isn't just about efficiency; it streamlines your entire computing experience. Windows' interface can be less than intuitive, hiding crucial settings within layers of menus. Fortunately, countless shortcuts exist
 How to Speed Up Your PC (Windows 11)May 11, 2025 pm 06:01 PM
How to Speed Up Your PC (Windows 11)May 11, 2025 pm 06:01 PMIs your Windows 11 PC running slower than usual? Opening apps and loading websites taking an eternity? You're not alone! This guide offers three simple, no-download solutions to boost your computer's performance without complex settings adjustments
 This Mini PC Doubles as a Not-So-Great TabletMay 11, 2025 am 06:01 AM
This Mini PC Doubles as a Not-So-Great TabletMay 11, 2025 am 06:01 AMThis mini PC, masquerading as a tablet, leaves much to be desired. The 7-inch, 1290x800 resolution screen is underwhelming. While some might use it for media consumption (similar to a 7-inch Amazon Fire Tablet), it's unlikely to be a primary choice
 Razer's New Basilisk Mobile & Joro Are for on-the-go GamingMay 11, 2025 am 03:02 AM
Razer's New Basilisk Mobile & Joro Are for on-the-go GamingMay 11, 2025 am 03:02 AMRazer launches the new Basilisk Mobile and Joro gaming keyboards, designed for mobile gamers. The Joro keyboard is small, but it comes with a full function key row and full-size arrow keys, providing a familiar and comfortable layout. The low button design helps maintain ergonomic hand posture and reduces fatigue caused by long-term gaming. Joro uses game-level keys to ensure fast and accurate key response and satisfying feedback, and enhances durability with durable UV-coated ABS keycaps. For competitive players, Joro also comes with Snap Tap mode, which improves first-person shooting game by allowing faster input between two keys without releasing the first key
 Lenovo's Legion 9i Gaming Laptop Has a Massive 18-Inch ScreenMay 10, 2025 pm 09:04 PM
Lenovo's Legion 9i Gaming Laptop Has a Massive 18-Inch ScreenMay 10, 2025 pm 09:04 PMLenovo's latest Legion 9i gaming laptop is a powerhouse, but portability might be a concern. This 10th-generation model boasts a groundbreaking 18-inch display, a first for the Legion 9i series. The screen offers stunning visuals, with up to 4K res
 You Can't Buy MSI's Latest Tiny PCMay 10, 2025 am 03:01 AM
You Can't Buy MSI's Latest Tiny PCMay 10, 2025 am 03:01 AMMSI Unveils Compact, Fanless Embedded PC: The MS-C927 For those who appreciate smaller-sized computers, MSI's latest offering, the MS-C927, is a noteworthy addition, though its aesthetics might not be award-winning. This fanless embedded PC is desig
 My Favorite Fidget Toys are Mechanical SwitchesMay 10, 2025 am 01:04 AM
My Favorite Fidget Toys are Mechanical SwitchesMay 10, 2025 am 01:04 AMThe crisp sound of the mechanical keyboard is pleasant, but it can only be heard when using the keyboard. These small and cheap stress-relieving toys solve this problem. Playing with the clicking stuff calmed me down—the sound was pleasant, and my hands were moving while focusing on other things. I used to do this with a telescopic pen (in the age when I needed to write my papers) which bothered my classmates. But now, mechanical keyboards and mechanical shafts bring the same effect. The clicking and sounds made by the mechanical shaft are pleasant, and the different feels and "clicking" of different mechanical shafts add to the satisfaction. Related ###### I am addicted to mechanical axes and keycaps, not collecting keyboards OK, maybe I'm just addicted to collecting anything clicking. Article 1


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SublimeText3 Linux new version
SublimeText3 Linux latest version

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

WebStorm Mac version
Useful JavaScript development tools

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool







