 Technology peripherals
Technology peripherals AI
AI Tencent Hunyuan joins forces with Hong Kong University of Science and Technology and Tsinghua University to launch 'Follow Your Emoji', turning photos into emoticons with one click
Tencent Hunyuan joins forces with Hong Kong University of Science and Technology and Tsinghua University to launch 'Follow Your Emoji', turning photos into emoticons with one clickTusheng Video has a new way to play.
Tencent Hunyuan, Hong Kong University of Science and Technology, and Tsinghua University jointly launched the portrait animation generation framework "Follow Your Emoji", which can generate any style of facial animation through facial skeleton information. Based on algorithm innovation and data accumulation, "Follow Your Emoji" can support refined control of the face, including eyebrows, eyes, eye rolls and other details. Animal emoticons can also be easily "manipulated".

Follow Your Emoji not only supports the generation of multiple portraits with a single expression, but also supports the generation of multiple expressions from a single portrait.

#In recent years, diffusion models have demonstrated better generative capabilities than older adversarial generative networks (GANs). Some methods utilize powerful basic diffusion models for high-quality video and image generation, but these basic models cannot directly preserve the identity features of the reference portrait during the animation process, causing the video results to show distortion and unrealistic artifacts. This is one of the main challenges of portrait animation tasks.

Figure: The overall flow chart of the paper, the upper part is the training process, and the lower part is the testing process
In this study, the researcher proposed a novel A diffusion model-based portrait animation framework for Follow-Your-Emoji. There are two major innovations in the algorithm.
This expression control signal can effectively guide animation generation. Researchers locate information through portrait (face) 3D keypoints. Since 3D keypoints have inherent canonical properties, they can effectively align target actions with reference portraits and avoid distortion that would lead to facial deformation in the generated video. This technology has a wide range of applications and can be used to produce facial morphing videos.
Secondly, the study also proposes a facial fine-grained loss function to help the model focus on capturing subtle expression changes and the detailed appearance of the portrait in the reference photo. Specifically, the author first uses the facial mask and expression mask and the author's expression perception signal, and then calculates the spatial distance between the ground truth value and the prediction result in these mask areas to achieve a high degree of restoration of the original portrait by the emoticon package.
In order to train the model, this study also constructed a high-quality expression training data set, which contains 18 exaggerated expressions and 20 minutes of real-life videos from 115 subjects. At the same time, the study adopts a progressive generation strategy, which enables the method to be extended to long-term animation synthesis with high fidelity and stability.

Figure: The quantitative experimental results and qualitative experimental results of the paper show that compared with the previous method, Follow-Your-Emoji can achieve better results
Finally, to address the lack of benchmarks in the field of portrait animation, the study also introduces a comprehensive benchmark called EmojiBench, which includes 410 portrait animation videos of various styles, showing a wide range of facial expressions and head poses. A comprehensive evaluation of Follow-YourEmoji using EmojiBench shows that the method performs well when dealing with portraits and actions outside the training domain, and performs better both quantitatively and qualitatively than existing baseline methods. Well, provides excellent visual fidelity identity representation and precise motion rendering.
Website: Follow-Your-Emoji: Freestyle Portrait Animation
Paper: [2406.01900] Follow-Your-Emoji: Fine-Controllable and Expressive Freestyle Portrait Animation
The above is the detailed content of Tencent Hunyuan joins forces with Hong Kong University of Science and Technology and Tsinghua University to launch 'Follow Your Emoji', turning photos into emoticons with one click. For more information, please follow other related articles on the PHP Chinese website!
 Let's Dance: Structured Movement To Fine-Tune Our Human Neural NetsApr 27, 2025 am 11:09 AM
Let's Dance: Structured Movement To Fine-Tune Our Human Neural NetsApr 27, 2025 am 11:09 AMScientists have extensively studied human and simpler neural networks (like those in C. elegans) to understand their functionality. However, a crucial question arises: how do we adapt our own neural networks to work effectively alongside novel AI s
 New Google Leak Reveals Subscription Changes For Gemini AIApr 27, 2025 am 11:08 AM
New Google Leak Reveals Subscription Changes For Gemini AIApr 27, 2025 am 11:08 AMGoogle's Gemini Advanced: New Subscription Tiers on the Horizon Currently, accessing Gemini Advanced requires a $19.99/month Google One AI Premium plan. However, an Android Authority report hints at upcoming changes. Code within the latest Google P
 How Data Analytics Acceleration Is Solving AI's Hidden BottleneckApr 27, 2025 am 11:07 AM
How Data Analytics Acceleration Is Solving AI's Hidden BottleneckApr 27, 2025 am 11:07 AMDespite the hype surrounding advanced AI capabilities, a significant challenge lurks within enterprise AI deployments: data processing bottlenecks. While CEOs celebrate AI advancements, engineers grapple with slow query times, overloaded pipelines, a
 MarkItDown MCP Can Convert Any Document into Markdowns!Apr 27, 2025 am 09:47 AM
MarkItDown MCP Can Convert Any Document into Markdowns!Apr 27, 2025 am 09:47 AMHandling documents is no longer just about opening files in your AI projects, it’s about transforming chaos into clarity. Docs such as PDFs, PowerPoints, and Word flood our workflows in every shape and size. Retrieving structured
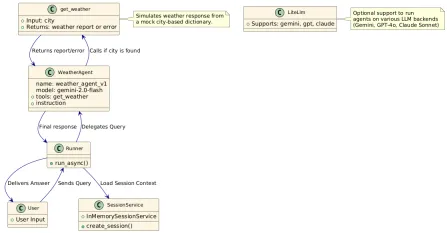 How to Use Google ADK for Building Agents? - Analytics VidhyaApr 27, 2025 am 09:42 AM
How to Use Google ADK for Building Agents? - Analytics VidhyaApr 27, 2025 am 09:42 AMHarness the power of Google's Agent Development Kit (ADK) to create intelligent agents with real-world capabilities! This tutorial guides you through building conversational agents using ADK, supporting various language models like Gemini and GPT. W
 Use of SLM over LLM for Effective Problem Solving - Analytics VidhyaApr 27, 2025 am 09:27 AM
Use of SLM over LLM for Effective Problem Solving - Analytics VidhyaApr 27, 2025 am 09:27 AMsummary: Small Language Model (SLM) is designed for efficiency. They are better than the Large Language Model (LLM) in resource-deficient, real-time and privacy-sensitive environments. Best for focus-based tasks, especially where domain specificity, controllability, and interpretability are more important than general knowledge or creativity. SLMs are not a replacement for LLMs, but they are ideal when precision, speed and cost-effectiveness are critical. Technology helps us achieve more with fewer resources. It has always been a promoter, not a driver. From the steam engine era to the Internet bubble era, the power of technology lies in the extent to which it helps us solve problems. Artificial intelligence (AI) and more recently generative AI are no exception
 How to Use Google Gemini Models for Computer Vision Tasks? - Analytics VidhyaApr 27, 2025 am 09:26 AM
How to Use Google Gemini Models for Computer Vision Tasks? - Analytics VidhyaApr 27, 2025 am 09:26 AMHarness the Power of Google Gemini for Computer Vision: A Comprehensive Guide Google Gemini, a leading AI chatbot, extends its capabilities beyond conversation to encompass powerful computer vision functionalities. This guide details how to utilize
 Gemini 2.0 Flash vs o4-mini: Can Google Do Better Than OpenAI?Apr 27, 2025 am 09:20 AM
Gemini 2.0 Flash vs o4-mini: Can Google Do Better Than OpenAI?Apr 27, 2025 am 09:20 AMThe AI landscape of 2025 is electrifying with the arrival of Google's Gemini 2.0 Flash and OpenAI's o4-mini. These cutting-edge models, launched weeks apart, boast comparable advanced features and impressive benchmark scores. This in-depth compariso


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

Notepad++7.3.1
Easy-to-use and free code editor





