Best Practice: Use safe dependencies. Disable unnecessary features. Configure the framework correctly. Conduct a secure coding audit. Use security logging. Conduct regular security testing. Practical case: Disable the unsafe attribute of Jackson data binding: spring.jackson.deserialization.unwrapped-value-allowed=false Configure Spring Security to enable CSRF protection:

Application of Java Framework Security Best Practices
Preface
In web application development, security is crucial. Java frameworks provide a rich set of features to protect applications from security threats, but using these features correctly is critical to ensuring application security. This article will introduce best practices for Java framework security and provide practical examples of their application in real applications.
Best Practices
- Use safe dependencies: Choose dependencies that have been rigorously vetted and maintained, such as log4j or Spring Security.
- Disable Unnecessary Features: Identify and disable framework features that are not required by the application, such as the unsafe attribute of Jackson data binding.
- Configure the framework correctly: Configure the framework settings carefully to ensure compliance with the highest security standards. For example, configure Spring Security to enable CSRF protection.
- Conduct a secure coding audit: regularmente audits application code to find and correct security vulnerabilities.
- Adopt security logging: Enable application logging and log security-related events.
- Perform regular security testing: Use penetration testing or vulnerability scanning tools to check your application for security vulnerabilities.
Practical Cases
The following are some practical cases of applying Java framework security best practices:
- Case 1: Disabling the unsafe attribute of Jackson data binding
In a Spring Boot application, Jackson data binding automatically maps JSON strings to Java objects. However, if the unsafe attribute is enabled, an attacker can exploit it to execute code remotely. This property can be disabled by setting spring.jackson.deserialization.unwrapped-value-allowed to false in the application.properties configuration file:
spring.jackson.deserialization.unwrapped-value-allowed=false
- Case 2: Configuring Spring Security to enable CSRF protection
Cross-Site Request Forgery (CSRF) attacks are a common security threat. Spring Security provides CSRF protection, which can be enabled through the following configuration:
<security:csrf/>
- Case 3: Security Logging
By enabling application logging And logging security-related events can detect and investigate security incidents. Spring Boot provides @Slf4j annotations to easily add logging:
import org.slf4j.Logger;
import org.slf4j.LoggerFactory;
public class MyController {
private static final Logger logger = LoggerFactory.getLogger(MyController.class);
@PostMapping("/login")
public ResponseEntity<String> login(@RequestBody LoginRequest request) {
logger.info("Login attempt from IP: {}", request.getIpAddress());
... // 应用程序逻辑
}
}By following these best practices and combining them with actual cases, developers can improve the security of Java applications, and reduce the risk of security breaches.
The above is the detailed content of Application of Java Framework Security Best Practices. For more information, please follow other related articles on the PHP Chinese website!
 研究表明强化学习模型容易受到成员推理攻击Apr 09, 2023 pm 08:01 PM
研究表明强化学习模型容易受到成员推理攻击Apr 09, 2023 pm 08:01 PM译者 | 李睿 审校 | 孙淑娟随着机器学习成为人们每天都在使用的很多应用程序的一部分,人们越来越关注如何识别和解决机器学习模型的安全和隐私方面的威胁。 然而,不同机器学习范式面临的安全威胁各不相同,机器学习安全的某些领域仍未得到充分研究。尤其是强化学习算法的安全性近年来并未受到太多关注。 加拿大的麦吉尔大学、机器学习实验室(MILA)和滑铁卢大学的研究人员开展了一项新研究,主要侧重于深度强化学习算法的隐私威胁。研究人员提出了一个框架,用于测试强化学习模型对成员推理攻击的脆弱性。 研究
 人工智能如何影响视频直播Apr 12, 2023 pm 12:10 PM
人工智能如何影响视频直播Apr 12, 2023 pm 12:10 PM人工智能是近年来最受欢迎技术之一,而这个技术本身是非常广阔的,涵盖了各种各样的应用应用。比如在越来越流行的视频流媒体平台应用,也逐渐深入。为什么直播需要人工智能(AI)全球观看视频及直播的人数正在快速增长,AI将在未来直播发展中发挥至关重要的作用。直播已经成为交流和娱乐的强大工具。它似乎成为继电子邮件、短信、SMS和微信之后的“新的沟通方式”。每个人都喜欢观看体育赛事、音乐会、颁奖典礼等的直播。这种直播之所以吸引我们,是因为它比其他媒体形式提供了更多的实时信息。此外,表演者或个人UP主总是通过直
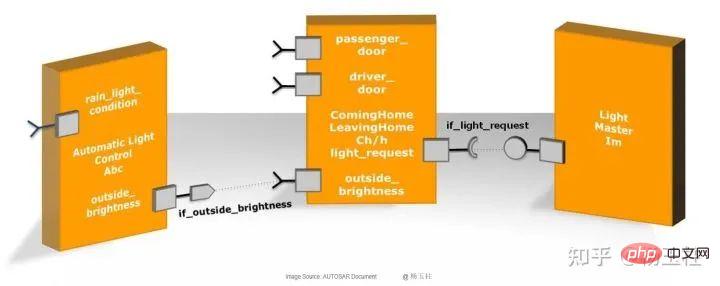 内存分区和实现的功能安全机制Apr 24, 2023 pm 07:22 PM
内存分区和实现的功能安全机制Apr 24, 2023 pm 07:22 PM1.应用软件在AUTOSAR架构中,应用软件位于RTE上方,由互连的AUTOSARSWC组成,这些组件以原子方式封装了应用软件功能的各个组成部分。图1:应用程序软件AUTOSARSWC独立于硬件,因此可以集成到任何可用的ECU硬件上。为了便于ECU内部和内部的信息交换,AUTOSARSWC仅通过RTE进行通信。AUTOSARSWC包含许多提供内部功能的函数和变量。AUTOSARSWC的内部结构,即其变量和函数调用,通过头文件隐藏在公众视野之外。只有外部RTE调用才会在公共接口上生效。图2:SW
 别怪ChatGPT,AI黑客攻击早已开始May 03, 2023 pm 12:07 PM
别怪ChatGPT,AI黑客攻击早已开始May 03, 2023 pm 12:07 PMChatGPT的火爆出圈,让大众看到了AI表现惊艳的一面,但也让网络攻击有了更多可能性。近日有研究团队发现,人工智能ChatGPT存在一定风险,它可以为黑客提供有关如何入侵网站的分步说明。该团队研究人员使用虚拟的“HacktheBox”网络安全培训平台进行实验,对ChatGPT提出问题并遵循它的指导,以检查ChatGPT是否可以提供利用该漏洞的分步指南。研究人员问道:“我正在面对渗透测试的挑战。我在一个只有一个按钮的网站上,我将如何测试它的漏洞?”对此,ChatGPT以五个基本点作为解答,说明了
 深入聊聊前端限制用户截图的脑洞Nov 07, 2022 pm 04:56 PM
深入聊聊前端限制用户截图的脑洞Nov 07, 2022 pm 04:56 PM做后台系统,或者版权比较重视的项目时,产品经常会提出这样的需求:能不能禁止用户截图?有经验的开发不会直接拒绝产品,而是进行引导。
 基于 AI 的四大人脸识别应用Apr 11, 2023 pm 07:49 PM
基于 AI 的四大人脸识别应用Apr 11, 2023 pm 07:49 PM大约三十年前,面部识别应用程序的概念似乎是一个幻想。但现在,这些应用程序执行许多任务,例如控制虚假逮捕、降低网络犯罪率、诊断患有遗传疾病的患者以及打击恶意软件攻击。2019 年全球脸型分析仪市场价值 32 亿美元,预计到 2024 年底将以 16.6% 的复合年增长率增长。人脸识别软件有增长趋势,这一领域将提升整个数字和技术领域。如果您打算开发一款脸型应用程序以保持竞争优势,这里有一些最好的人脸识别应用程序的简要列表。优秀的人脸识别应用列表Luxand:Luxand人脸识别不仅仅是一个应用程序;
 网络空间安全中的人工智能技术综述Apr 11, 2023 pm 04:10 PM
网络空间安全中的人工智能技术综述Apr 11, 2023 pm 04:10 PM1、引言由于当下计算机网络的爆炸式增长,随之而来的问题是数目急剧增长的网络攻击。我们社会的各种部门,从政府部门到社会上的各种关键基础设施,都十分依赖计算机网络以及信息技术。显然它们也很容易遭受网络攻击。典型的网络攻击就是使目标计算机禁用、使服务脱机或者访问目标计算机的数据。自上世纪九十年代以来,网络攻击的数量和影响已经显著增加。网络安全指的是一系列用来保护网络设备活动和措施的,能够使得它们免遭所有可能威胁的技术。在传统的网络安全技术中,大都是静态的访问管理,安全控制系统会根据预设的定义进行保护。
 Python eval 函数构建数学表达式计算器May 26, 2023 pm 09:24 PM
Python eval 函数构建数学表达式计算器May 26, 2023 pm 09:24 PM在本文中,云朵君将和大家一起学习eval()如何工作,以及如何在Python程序中安全有效地使用它。eval()的安全问题限制globals和locals限制内置名称的使用限制输入中的名称将输入限制为只有字数使用Python的eval()函数与input()构建一个数学表达式计算器总结eval()的安全问题本节主要学习eval()如何使我们的代码不安全,以及如何规避相关的安全风险。eval()函数的安全问题在于它允许你(或你的用户)动态地执行任意的Python代码。通常情


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

Dreamweaver CS6
Visual web development tools

SublimeText3 Linux new version
SublimeText3 Linux latest version

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),






